Authentication
Overview
About security credentials
When using APIs through the Payments Developer Portal, you must use certificates for:
- Authentication - to confirm your identity.
- Authorization - to confirm your permissions.
In addition, you may be asked to provide certificates for:
- Signing requests, especially POST requests.
- Encrypting personal data.
- Receiving callbacks.
Depending on your chosen product, you may be asked to provide one or more of the following types of certificates:
- Transport Certificate (also called mTLS Certificate) - Provided by an approved Certification Authority (CA). This is an SSL authentication certificate that confirms the identity of a host running your application but does not carry any access permissions.
- For information on making requests to J.P. Morgan APIs, see mTLS with Digital Signature.
- Digital Signature Certificate - For certain API requests, such as POST requests, you may be required to include a Digital Signature Certificate which you use to “sign” your requests. This is an additional layer of security that relies on asymmetric cryptography, just like OAuth with Signed JWT Assertions.
- For information on making requests to J.P. Morgan APIs, see mTLS with Digital Signature.
- Open Authorization (OAuth) Access Token - OAuth is an authorization standard that allows applications to access another application's resources. OAuth access tokens confirm both access identity and permissions. There are two ways of obtaining an OAuth access token:
- OAuth with Basic Authentication uses client id and client secret in Mock environments.
- OAuth with Signed JWT Assertion uses asymmetric cryptography* in Testing and Production environments.
*Asymmetric cryptography is used to sign "JWT Assertions" that are sent to confirm the identity of a host that has access to a private key. The public key for this authentication mechanism can be shared in the form of a certificate and can be used to verify the signatures of the "JWT Assertions" produced by the host. - For information on making requests to J.P. Morgan APIs, see OAuth.
- Callback Certificate - The Callback Certificate is a way to give permission to J.P. Morgan services to send updates as they occur, not only when you have sent an API request. It permits asynchronous connection to your system.
- Encryption Certificate - The Encryption Certificate allows for an additional layer of security in which you encrypt the request payload. J.P. Morgan supports encryption at multiple levels such as at the Request level and/or at PII Data only, which encrypts data in your payload.
For additional information on creating certificates and configuring credentials for API access, refer to the "Getting Started” page of the API documentation in which you are interested in using.
About callbacks
A callback occurs when J.P. Morgan sends event updates asynchronously to your system for the product you are using. To enable callbacks, you must submit your callback URL and authentication certificate via the Payments Developer Portal.
The following diagram illustrates the request, response, and callback communication between your application and callback handle and the J.P. Morgan service.
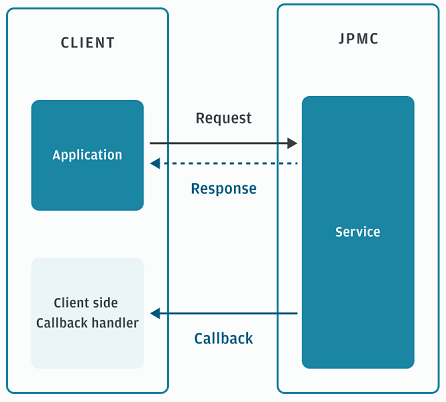
Certificates needed for callbacks
You are required to upload a Callback Certificate and optionally, an Encryption Certificate, to the Payments Developer Portal.
For a callback, J.P. Morgan issues a Callback Certificate and a Digital Signature Certificate.
Setup authentication
Generate a signed certificate using a Certificate Authority (CA)
CA-signed certificates must be signed by a J.P. Morgan approved certificate authority.
Follow the instructions from your selected certificate authority for generating a certificate.
Once you recieve the certificate from the CA, then upload the certificate to the Payments Developer Portal under the Security page within a project.
Add security certificates
When you have products available for the Client Testing and Production environments, you can add the security certificates required to send requests to J.P. Morgan APIs.
- In the Payments Developer Portal, navigate to the Security page.
- For the environment you plan to use, select the corresponding tab.
- In the Request section, click Add Security.
The "Add certificate" dialog appears. - For the "Certificate use" dropdown, select the type of security certificate you wish to upload.
- In the "Certificate upload" box, drag and drop, or browse for the desired certificate, for example, MTLS, Digital signature, or OAuth 2.0.
- Click Add Certificate..
The "Add security" dialog closes and the added certificate is listed.
You have completed the API security requirements. You can start sending API requests in your chosen environments.
Add callback URL and certificates
J.P. Morgan requires authentication for callbacks to protect communication with clients.
To add an authentication certificate:
- Navigate to the Global Payments screen, Security tab and select your environment.
- Under Response, in the Callbacks section, click Configure callbacks.
The Configure Callbacks dialog appears. - In the Configure Callbacks dialog, enter your callback URL.
- Select the existing certificate if it is your desired choice or use the Drag and drop or Browse box to upload your desired choice.
- Click Configure callbacks.
The Configure Callbacks dialog closes.
You have added your callback URL and certificate.
Reference of approved list of certificate authorities
J.P. Morgan supports the X.509 International Telecommunication Union standard for the format of public key certificates. In order to use SSL certificates, you must provide J.P. Morgan with UAT and Production certificates issued by one of the listed approved certificate authorities. These certificates should be installed on your server - J.P. Morgan installs them on theirs. You must use a listed approved Root Certificate and Intermediate Certificate.
The validity date for a certificate cannot be greater than one year from the issue date.
Approved root certificates
Some CAs may no longer include the Client Authentication EKU by default, with full depreciation planned for a later date. Contact the CAs directly to confirm whether this setting can still be enabled upon request.
The following is the approved list of root certificates, inclluding the issuing authority, certificate name, and thumbprint.
| Authority | Certificate Name | SHA-1 Thumbprint |
|---|---|---|
| Amazon | AmazonRootCA3 | 0d 44 dd 8c 3c 8c 1a 1a 58 75 64 81 e9 0f 2e 2a ff b3 d2 6e |
| Amazon | AmazonRootCA4 | f6 10 84 07 d6 f8 bb 67 98 0c c2 e2 44 c2 eb ae 1c ef 63 be |
| Amazon | Amazon-SFSRootCAG2 | 92 5a 8f 8d 2c 6d 04 e0 66 5f 59 6a ff 22 d8 63 e8 25 6f 3f |
| Amazon | AmazonRootCA1 | 8d a7 f9 65 ec 5e fc 37 91 0f 1c 6e 59 fd c1 cc 6a 6e de 16 |
| Amazon | AmazonRootCA2 | 5a 8c ef 45 d7 a6 98 59 76 7a 8c 8b 44 96 b5 78 cf 47 4b 1a |
| DigiCert | DigiCertRSA4096RootG5 | 87 b8 e6 d3 8f 1a 39 cd 97 f0 4a 9e 17 4b 3c 9e e7 ee 11 15 |
| DigiCert | DigiCertSMIMEECCP384RootG5 | 5b c5 ad e2 9a a7 54 da 84 89 53 a5 fe d7 5b 46 86 d0 57 08 |
| DigiCert | DigiCertSMIMERSA4096RootG5 | 1c b8 a7 08 c9 0d 20 79 01 a0 b2 36 7f f0 95 65 e4 53 24 fe |
| DigiCert | DigiCertTLSECCP384RootG5 | 17 f3 de 5e 9f 0f 19 e9 8e f6 1f 32 26 6e 20 c4 07 ae 30 ee |
| DigiCert | DigiCertTLSRSA4096RootG5 | a7 88 49 dc 5d 7c 75 8c 8c de 39 98 56 b3 aa d0 b2 a5 71 35 |
| DigiCert | DigiCertTrustedRootG4 | dd fb 16 cd 49 31 c9 73 a2 03 7d 3f c8 3a 4d 7d 77 5d 05 e4 |
| DigiCert | DigiCertAssuredIDRootCA | 05 63 b8 63 0d 62 d7 5a bb c8 ab 1e 4b df b5 a8 99 b2 4d 43 |
| DigiCert | DigiCertAssuredIDRootG2 | a1 4b 48 d9 43 ee 0a 0e 40 90 4f 3c e0 a4 c0 91 93 51 5d 3f |
| DigiCert | DigiCertAssuredIDRootG3 | f5 17 a2 4f 9a 48 c6 c9 f8 a2 00 26 9f dc 0f 48 2c ab 30 89 |
| DigiCert | DigiCertCSECCP384RootG5 | 84 35 73 11 2a 3b 31 93 44 e5 e4 ec ab c9 f2 6c 7c d5 4d 07 |
| DigiCert | DigiCertCSRSA4096RootG5 | 5e ee d8 6f a3 7c 67 52 30 64 2f 55 c8 4d db f6 7c d3 3c 80 |
| DigiCert | DigiCertECCP384RootG5 | d1 ee b1 e8 c0 90 20 ba b8 5d 3d e2 7f 78 ee 33 a0 6c ae db |
| DigiCert | DigiCertFederatedIDRootCA | 8e 93 4f 88 a5 a4 55 33 36 e2 9b 5f b8 66 60 48 ef aa 82 40 |
| DigiCert | DigiCertGlobalRootCA | a8 98 5d 3a 65 e5 e5 c4 b2 d7 d6 6d 40 c6 dd 2f b1 9c 54 36 |
| DigiCert | DigiCertGlobalRootG2 | df 3c 24 f9 bf d6 66 76 1b 26 80 73 fe 06 d1 cc 8d 4f 82 a4 |
| DigiCert | DigiCertGlobalRootG3 | 7e 04 de 89 6a 3e 66 6d 00 e6 87 d3 3f fa d9 3b e8 3d 34 9e |
| DigiCert | DigiCertHighAssuranceEVRootCA | 5f b7 ee 06 33 e2 59 db ad 0c 4c 9a e6 d3 8f 1a 61 c7 dc 25 |
| DigiCert | VeriSign Class 3 Public Primary Certification Authority - G5 | 4e b6 d5 78 49 9b 1c cf 5f 58 1e ad 56 be 3d 9b 67 44 a5 e5 |
| Entrust | Entrust Root Certification Authority - G2 | 8c f4 27 fd 79 0c 3a d1 66 06 8d e8 1e 57 ef bb 93 22 72 d4 |
| GlobalSign | GlobalSign-rootr46 | 53 a2 b0 4b ca 6b d6 45 e6 39 8a 8e c4 0d d2 bf 77 c3 a2 90 |
| GlobalSign | GlobalSign-timestamproote46 | 3a cc 40 d9 b9 dc 16 fe a0 c1 06 13 47 67 d0 f6 83 b2 27 93 |
| GlobalSign | GlobalSign-timestamprootr45 | 13 9b 1c 71 2f d1 7c 3c a5 da 6e 57 01 af ba 01 58 f9 d4 5d |
| GlobalSign | GlobalSign-codesigningroote45 | 79 aa 50 5e dd 09 b3 21 e3 6d 57 91 0a 5d f5 a9 fb 85 cc 57 |
| GlobalSign | GlobalSign-codesigningrootr45 | 4e fc 31 46 0c 61 9e ca e5 9c 1b ce 2c 00 80 36 d9 4c 84 b8 |
| GlobalSign | GlobalSign-roote46 | 39 b4 6c d5 fe 80 06 eb e2 2f 4a bb 08 33 a0 af db b9 dd 84 |
| GlobalSign | GlobalSign-Root-R1 | b1 bc 96 8b d4 f4 9d 62 2a a8 9a 81 f2 15 01 52 a4 1d 82 9c |
| GlobalSign | GlobalSign-Root-R3 | d6 9b 56 11 48 f0 1c 77 c5 45 78 c1 09 26 df 5b 85 69 76 ad |
| GlobalSign | GlobalSign Root CA - R6 | 80 94 64 0e b5 a7 a1 ca 11 9c 1f dd d5 9f 81 02 63 a7 fb d1 |
| GoDaddy | Go Daddy Root Certificate Authority - G2 | 47 be ab c9 22 ea e8 0e 78 78 34 62 a7 9f 45 c2 54 fd e6 8b |
| GoDaddy | GoDaddy-gd-class2-root | 27 96 ba e6 3f 18 01 e2 77 26 1b a0 d7 77 70 02 8f 20 ee e4 |
| GoDaddy | GoDaddy-sfroot-g2 | b5 1c 06 7c ee 2b 0c 3d f8 55 ab 2d 92 f4 fe 39 d4 e7 0f 0e |
| Google-r1 | e5 8c 1c c4 91 3b 38 63 4b e9 10 6e e3 ad 8e 6b 9d d9 81 4a | |
| Google-r2 | 9a 44 49 76 32 db de fa d0 bc fb 5a 7b 17 bd 9e 56 09 24 94 | |
| Google-r3 | ed e5 71 80 2b c8 92 b9 5b 83 3c d2 32 68 3f 09 cd a0 1e 46 | |
| Google-r4 | 77 d3 03 67 b5 e0 0c 15 f6 0c 38 61 df 7c e1 3b 92 46 4d 47 | |
| Google-gsr4 | 6b a0 b0 98 e1 71 ef 5a ad fe 48 15 80 77 10 f4 bd 6f 0b 28 | |
| JPMorgan Chase | JPMC Root CA | 1a 58 c1 67 02 09 45 31 0f 25 e9 90 b9 94 cd 59 c8 f2 6b a5 |
| Let's Encrypt | ISRG Root X1 | ca bd 2a 79 a1 07 6a 31 f2 1d 25 36 35 cb 03 9d 43 29 a5 e8 |
| Let's Encrypt | ISRG Root X2 | bd b1 b9 3c d5 97 8d 45 c6 26 14 55 f8 db 95 c7 5a d1 53 af |
| Microsoft | Microsoft RSA Root Certificate Authority 2017 | 73 a5 e6 4a 3b ff 83 16 ff 0e dc cc 61 8a 90 6e 4e ae 4d 74 |
| Microsoft | Microsoft Time Stamp Root Certificate Authority 2014 | 01 19 e8 1b e9 a1 4c d8 e2 2f 40 ac 11 8c 68 7e cb a3 f4 d8 |
| Microsoft | Microsoft-MicRooCerAut_2010-06-23 | 3b 1e fd 3a 66 ea 28 b1 66 97 39 47 03 a7 2c a3 40 a0 5b d5 |
| Microsoft | Microsoft-MicRooCerAut2011_2011_03_22 | 8f 43 28 8a d2 72 f3 10 3b 6f b1 42 84 85 ea 30 14 c0 bc fe |
| Microsoft | Microsoft-Symantec Enterprise Mobile Root for Microsoft | 92 b4 6c 76 e1 30 54 e1 04 f2 30 51 7e 6e 50 4d 43 ab 10 b5 |
| Microsoft | Microsoft ECC Product Root Certificate Authority 2018 | 06 f1 aa 33 0b 92 7b 75 3a 40 e6 8c df 22 e3 4b cb ef 33 52 |
| Microsoft | Microsoft ECC Root Certificate Authority 2017 | 99 9a 64 c3 7f f4 7d 9f ab 95 f1 47 69 89 14 60 ee c4 c3 c5 |
| Microsoft | Microsoft ECC TS Root Certificate Authority 2018 | 31 f9 fc 8b a3 80 59 86 b7 21 ea 72 95 c6 5b 3a 44 53 42 74 |
| Microsoft | Microsoft EV ECC Root Certificate Authority 2017 | b8 09 5f 5a 89 fb 47 a7 01 7e d7 94 dd 4f 61 1e 27 83 0e 27 |
| Microsoft | Microsoft EV RSA Root Certificate Authority 2017 | 3a d3 8a 39 ce 4e 88 dc df 46 99 5e 96 9f c3 39 d0 79 98 58 |
| Microsoft | Microsoft Identity Verification Root Certificate Authority 2020 | f4 00 42 e2 e5 f7 e8 ef 81 89 fe d1 55 19 ae ce 42 c3 bf a2 |
| Microsoft | Microsoft Public RSA Timestamping CA 2020 | 27 f0 ab ac 28 77 ba 25 5f 62 b3 89 b4 3f f5 39 a0 fb 59 8e |
| Sectigo | AAA Certificate Services | d1 eb 23 a4 6d 17 d6 8f d9 25 64 c2 f1 f1 60 17 64 d8 e3 49 |
| Sectigo | COMODO ECC Certification Authority | 9f 74 4e 9f 2b 4d ba ec 0f 31 2c 50 b6 56 3b 8e 2d 93 c3 11 |
| Sectigo | COMODO RSA Certification Authority | af e5 d2 44 a8 d1 19 42 30 ff 47 9f e2 f8 97 bb cd 7a 8c b4 |
| Sectigo | Sectigo Public Server Authentication Root E46 | ec 8a 39 6c 40 f0 2e bc 42 75 d4 9f ab 1c 1a 5b 67 be d2 9a |
| Sectigo | Sectigo Public Server Authentication Root R46 | ad 98 f9 f3 e4 7d 75 3b 65 d4 82 b3 a4 52 17 bb 6e f5 e4 38 |
| Sectigo | USERTrust ECC Certification Authority | d1 cb ca 5d b2 d5 2a 7f 69 3b 67 4d e5 f0 5a 1d 0c 95 7d f0 |
| Sectigo | USERTrust RSA Certification Authority.PEM | 2b 8f 1b 57 33 0d bb a2 d0 7a 6c 51 f7 0e e9 0d da b9 ad 8e |
| SSL.com | SSLcom-RootCA-EV-RSA-4096-R2 | 74 3a f0 52 9b d0 32 a0 f4 4a 83 cd d4 ba a9 7b 7c 2e c4 9a |
| SSL.com | SSLcom-RootCA-EV-RSA-4096-R3 | d5 b2 49 cd ff 5b 61 cf e1 b3 04 36 14 7a 76 33 0c 81 3b 36 |
| SSL.com | SSLcom-RootCA-RSA-4096-R2 | 8e 4d b2 78 e7 f7 7c 94 77 bb 25 af b2 65 57 ed d8 1d 51 2a |
| SSL.com | SSLcomRootCertificationAuthorityECC | c3 19 7c 39 24 e6 54 af 1b c4 ab 20 95 7a e2 c3 0e 13 02 6a |
| SSL.com | SSLcomRootCertificationAuthorityRSA | b7 ab 33 08 d1 ea 44 77 ba 14 80 12 5a 6f bd a9 36 49 0c bb |
| SSL.com | SSLcom-TLS-Root-2022-ECC | 9f 5f d9 1a 54 6d f5 0c 71 f0 ee 7a bd 17 49 98 84 73 e2 39 |
| SSL.com | SSLcom-TLS-Root-2022-RSA | ec 2c 83 40 72 af 26 95 10 ff 0e f2 03 ee 31 70 f6 78 9d ca |
| SSL.com | SSLcom-CodeSigning-Root-2022-ECC | 0d 9e 9a b2 07 65 a8 9e d9 cd 8d f2 c7 a6 3b c7 74 95 ef 31 |
| SSL.com | SSLcom-CodeSigning-Root-2022-RSA | d4 69 52 84 cd 17 98 d9 cb 16 99 46 4c 06 49 94 c4 e2 bb fd |
| SSL.com | SSLcomEVRootCertificationAuthorityECC | 4c dd 51 a3 d1 f5 20 32 14 b0 c6 c5 32 23 03 91 c7 46 42 6d |
| SSL.com | SSLcom-RootCA-ECC-384-R2.cer | c4 ab a3 e9 60 24 c0 42 a5 e0 3b b0 68 41 1d 4e ce 99 7d 55 |
| SSL.com | SSLcom-RootCA-EV-ECC-384-R2.cer | fc 8e 2c bc 87 41 5a b6 49 a0 0c ea 08 f5 11 ba c9 ac 26 5c |
Approved intermediate certificates
The approved list of Intermediate Certificates with the authority, name, and footprint:
| Authority | Certificate Name | SHA-1 Thumbprint |
|---|---|---|
| DigiCert | DigiCert SHA2 Extended Validation Server CA | 7e 2f 3a 4f 8f e8 fa 8a 57 30 ae ca 02 96 96 63 7e 98 6f 3f |
| DigiCert | DigiCert Global CA G2 | d6 ae e3 16 31 f7 ab c5 6b 9d e8 ab ec cc 41 08 a6 26 b1 04 |
| DigiCert | DigiCert SHA2 Secure Server CA | 1f b8 6b 11 68 ec 74 31 54 06 2e 8c 9c c5 b1 71 a4 b7 cc b4 |
| DigiCert (RapidSSL) | RapidSSL RSA CA 2018 | 98 c6 a8 dc 88 79 63 ba 3c f9 c2 73 1c bd d3 f7 de 05 ac 2d |
| DigiCert (Thawte) | Thawte RSA CA 2018 | 4d ee a7 06 0d 80 ba bf 16 43 b4 e0 f0 10 4c 82 99 50 75 b7 |
| Entrust | Entrust Certification Authority - L1K | f2 1c 12 f4 6c db 6b 2e 16 f0 9f 94 19 cd ff 32 84 37 b2 d7 |
| GeoTrust (RapidSSL) | RapidSSL SHA256 CA | c8 6e db c7 1a b0 50 78 f6 1a cd f3 d8 dc 5d b6 1e b7 5f b6 |
| GlobalSign | GlobalSign PersonalSign 1 CA - SHA256 - G3 | 5e c2 8e d7 9e 8c e8 5d 8f 84 cd 7a a7 b8 6d 73 b1 71 de b9 |
| GlobalSign (AlphaSSL) | AlphaSSL CA - SHA256 - G2 | 4c 27 43 17 17 56 5a 3a 07 f3 e6 d0 03 2c 42 58 94 9c f9 ec |
| GoDaddy | Go Daddy Secure Certificate Authority - G2 | 27 ac 93 69 fa f2 52 07 bb 26 27 ce fa cc be 4e f9 c3 19 b8 |
| Sectigo | Trusted Secure Certificate Authority 5 | 52 5c 47 fb 3a 5e 06 55 fb d4 be 96 3c a1 e9 4d 5f ec b4 3d |
| D-Trust | D-TRUST Test CA 2-1 2018 | 28 64 f0 a4 a0 46 eb 06 32 e2 36 41 fc d1 0e 96 9d 92 e8 09 |
| Actalis | Actalis Extended Validation Server CA G1 Test | 70 27 77 15 df 7c b3 6a 92 70 af 82 b1 86 98 4f e6 2b 4d 76 |
| Government of Netherlands G3 | Staat der Nederlanden Organisatie Services CA - G3 | 32 ea 2e 21 00 d1 9b da a8 cb 9b 77 24 cc 86 14 15 ab ed 9d |
| Government of Netherlands G3 | QuoVadis PKIoverheid Organisatie Server CA - G3 | c7 62 08 49 eb c2 fd 41 e8 02 57 bb d0 05 94 8f b7 2d e1 16 |
| DST | Let's Encrypt Authority X3 | e6 a3 b4 5b 06 2d 50 9b 33 82 28 2d 19 6e fe 97 d5 95 6c cb |
| Sectigo | USERTrust RSA Certification Authority | ea b0 40 68 9a 0d 80 5b 5d 6f d6 54 fc 16 8c ff 00 b7 8b e3 |
| Sectigo | Sectigo RSA Domain Validation Secure Server CA | 33 e4 e8 08 07 20 4c 2b 61 82 a3 a1 4b 59 1a cd 25 b5 f0 db |
| Sectigo | Sectigo RSA Organization Validation Secure Server CA | 40 ce f3 04 6c 91 6e d7 ae 55 7f 60 e7 68 42 82 8b 51 de 53 |
| DigiCert | DigiCert SHA2 Assured ID CA | e1 2d 2e 8d 47 b6 4f 46 9f 51 88 02 df bd 99 c0 d8 6d 3c 6a |
| Encryption Everywhere | Encryption Everywhere DV TLS CA - G1 | 59 4f 2d d1 03 52 c2 36 01 38 ee 35 aa 90 6f 97 3a a3 0b d3 |
| GeoTrust | GeoTrust CN RSA CA G1 | ab cb 71 01 35 6f 9e 4e 7a 44 99 88 e4 30 0b d0 3b 32 1f 95 |
| Digicert | DigiCert SHA2 High Assurance Server CA | a0 31 c4 67 82 e6 e6 c6 62 c2 c8 7c 76 da 9a a6 2c ca bd 8e |
| GlobalSign | GlobalSign Organization Validation CA - SHA256 - G2 | 90 2e f2 de eb 3c 5b 13 ea 4c 3d 51 93 62 93 09 e2 31 ae 55 |
| GlobalSign | GlobalSign RSA DV SSL CA 2018 | a4 16 00 23 31 a4 e0 c8 c5 3d 94 ac 1e 02 34 72 3d 8b de 97 |
| GlobalSign | GlobalSign RSA OV SSL CA 2018 | df e8 30 23 06 2b 99 76 82 70 8b 4e ab 8e 81 9a ff 5d 97 75 |
| Entrust | Entrust Certification Authority - L1M | cc 13 66 95 63 90 65 fa b4 70 74 d2 8c 55 31 4c 66 07 7e 90 |
| Sectigo | Sectigo RSA Extended Validation Secure Server CA | a3 df 96 6d 0c b2 d8 4a f8 f1 6c 85 5b 97 c4 93 64 f5 d8 c0 |
| Secure Site CA G2 | Secure Site CA G2 | 8d 88 8b 3c ae 20 c7 4f 4c e1 b3 0b f5 1e e3 6e ab 56 2c de |
| Amazon | Starfield Class 2 Certification Authority | ad 7e 1c 28 b0 64 ef 8f 60 03 40 20 14 c3 d0 e3 37 0e b5 8a |
| Amazon | Starfield Services Root Certificate Authority - G2 | 9e 99 a4 8a 99 60 b1 49 26 bb 7f 3b 02 e2 2d a2 b0 ab 72 80 |
| Amazon | Amazon Root CA 1 | 06 b2 59 27 c4 2a 72 16 31 c1 ef d9 43 1e 64 8f a6 2e 1e 39 |
| Amazon | Amazon | 91 7e 73 2d 33 0f 9a 12 40 4f 73 d8 be a3 69 48 b9 29 df fc |
| DigiCert | TrustAsia TLS RSA CA | ec 41 91 d1 f3 57 bd 53 94 83 28 6f a6 7f d2 19 14 3d 26 11 |
| DigiCert | DigiCert EV RSA CA G2 | 09 0a 16 f9 ba 16 00 1b 2e c1 30 f8 05 23 e5 b5 eb 25 91 58 |
| DigiCert | GeoTrust EV RSA CA 2018 | a3 99 04 64 17 b6 7e 32 0d 3e fa 69 d7 dc e6 b8 bf e8 a9 f2 |
| JPMC | PSIN0P551 | 35 1e 74 b2 98 01 21 1c 5e 16 58 95 b6 34 20 b4 f7 9c 26 fd |
| Government of Netherlands G1 | Staat der Nederlanden Private Services CA - G1 | 03 67 7b 4e c0 ff ca 9d 3c ad 6c 04 4a 73 3b 3e 7a 75 d1 fd |
| Government of Netherlands G1 | QuoVadis PKIoverheid Private Services CA - G1 | 99 61 61 ab 19 f7 76 d8 81 78 c6 23 f8 52 9e 5a 64 a6 f8 ef |
| DigiCert (RapidSSL) | RapidSSL TLS DV RSA Mixed SHA256 2020 CA-1 | 9b d0 8a 58 87 6f 6c 84 9d b6 bb 99 a8 b1 94 89 26 47 86 0e |
| DigiCert | DigiCert Global CA-3 G2 | 10 84 c3 32 26 b4 8d 7c 0b fe d8 21 80 aa b1 dd d8 44 b2 83 |
| DigiCert | DigiCert ECC Secure Server CA | 56 ee 7c 27 06 83 16 2d 83 ba ea cc 79 0e 22 47 1a da ab e8 |
| DigiCert | DigiCert TLS RSA SHA256 2020 CA1 | 69 38 fd 4d 98 ba b0 3f aa db 97 b3 43 96 83 1e 37 80 ae a1 |
| DST | R3 | 48 50 4e 97 4c 0d ac 5b 5c d4 76 c8 20 22 74 b2 4c 8c 71 72 |
| Sectigo | USERTrust RSA Certification Authority | d8 9e 3b d4 3d 5d 90 9b 47 a1 89 77 aa 9d 5c e3 6c ee 18 4c |
| DigiCert | DigiCert Global G2 TLS RSA SHA256 2020 CA1 | 1d 73 22 b4 1e d9 9f dd 68 51 1b ab 78 6c 8e 26 e0 83 1b 3b |
| GlobalSign | GlobalSign GCC R3 DV TLS CA 2020 | 1c 61 0a 0a 87 d4 92 f4 83 22 c2 af d3 be 9b 6a d3 6b 6b ee |
| DigiCert | DigiCert Secure Site CN CA G3 | 44 79 f6 9c 9b e9 c3 94 b9 f1 72 11 aa 6d 6d a8 14 3d b6 9c |
| DigiCert | DigiCert SHA2 Assured ID Code Signing CA | 92 c1 58 8e 85 af 22 01 ce 79 15 e8 53 8b 49 2f 60 5b 80 c6 |
| DigiCert | GeoTrust RSA CA 2018 | 7c cc 2a 87 e3 94 9f 20 57 2b 18 48 29 80 50 5f a9 0c ac 3b |
| DigiCert | GeoTrust TLS DV RSA Mixed SHA256 2020 CA-1 | b2 c2 f9 fc 3a 06 f3 a5 e8 42 89 2a f9 c6 4e d4 77 8b e0 18 |
| Sectigo | InCommon RSA Server CA | f5 fb 01 de a6 e5 9c a6 dd 05 70 54 f4 a3 ff 72 dd e1 d5 c6 |
| Sectigo | Network Solutions DV Server CA 2 | 90 85 4c e5 74 d0 32 18 df 2e 7b 4a 05 4a a5 3f 69 51 c1 d2 |
| QuoVadis | QuoVadis Global SSL ICA G3 | b2 ec 15 c7 05 c6 6e 4d 30 c3 3a 17 f3 df 5b cc 11 3f d9 63 |
| DigiCert | GeoTrust TLS DV RSA Mixed SHA256 2020 CA-1 | 2f 7a a2 d8 60 56 a8 77 57 96 f7 98 c4 81 a0 79 e5 38 e0 04 |
| COMODO CA | ZeroSSL RSA Domain Secure Site CA | c8 1a 8b d1 f9 cf 6d 84 c5 25 f3 78 ca 1d 3f 8c 30 77 0e 34 |
| Sectigo | COMODO RSA Organization Validation Secure Server CA | 10 4c 63 d2 54 6b 80 21 dd 10 5e 9f ba 5a 8d 78 16 9f 6b 32 |
| COMODO CA | Gandi Pro SSL CA 2 | 72 27 6f a9 27 54 59 0c b8 24 e8 fa d4 71 59 75 fa 31 6b 33 |
| JPMC | PSIN0P551 | 4f 74 1b d2 e1 3a 18 a5 11 e6 8b 6d fc 51 97 ff 30 2c e5 49 |
| Entrust | Entrust Code Signing Root Certification Authority - CSB | b3 37 b8 fd b5 6e cb 58 bf 5d bc f8 c2 2c 32 01 07 53 5a 02 |
| Entrust | Entrust Extended Validation Code Signing CA - EVCS2 | b5 20 63 ce cf fa fa 24 b5 79 93 b8 ef e7 fb 1e 4d 6d 56 bc |
| Sectigo | Sectigo Public Code Signing Root R46 | 32 9b 78 a5 c9 eb c2 04 32 42 de 90 ce 1b 7c 6b 1b a6 c6 92 |
| Sectigo | Sectigo Public Code Signing CA R36 | 0b c5 e7 67 73 d2 e4 4f c9 90 3d 4d fe fe 45 15 53 bb ec 4a |
| DigiCert | GeoTrust TLS RSA CA G1 | 8b 3c 5b 9b 86 7d 4b e4 6d 1c b5 a0 1d 45 d6 7d c8 e9 40 82 |
| DigiCert | RapidSSL Global TLS RSA 4096 SHA256 2022 CA1 | 68 f2 2b 1a 62 98 f7 da 19 1e 61 49 ed 8d e0 ef ff 54 ad 8c |
| Sectigo | Gandi Standard SSL CA 2 | 24 71 06 a4 05 b2 88 a4 6e 70 a0 26 27 17 16 2d 09 03 e7 34 |
| Sectigo | TrustAsia RSA DV TLS CA G2 | f3 4d de cf 3e a1 0b d2 e2 f6 30 8e d1 ce 53 7b 09 35 78 b3 |
| DigiCert | DigiCert Assured ID Client CA G2 | 7c 77 03 57 09 96 59 b4 0d a4 c4 ba 67 78 5d 54 23 a0 13 c8 |
| GlobalSign | GlobalSign Extended Validation CA - SHA256 - G3 | 60 23 19 2f e7 b5 9d 27 89 13 0a 9f e4 09 4f 9b 55 70 d4 a2 |
| IdenTrust | HydrantID Server CA O1 | 3c 97 cb b4 49 1f c8 d6 3d 12 b4 89 0c 28 54 81 64 19 8e db |
| DigiCert | DigiCert Trusted G4 Code Signing RSA4096 SHA384 2021 CA1 | 7b 0f 36 0b 77 5f 76 c9 4a 12 ca 48 44 5a a2 d2 a8 75 70 1c |
| DigiCert | GeoTrust Global TLS RSA4096 SHA256 2022 CA1 | 7e 6d b7 b7 58 4d 8c f2 00 3e 09 31 e6 cf c4 1a 3a 62 d3 df |
| DigiCert | Thawte TLS RSA CA G1 | c9 fe fc 76 3d 95 48 b4 87 69 6f 04 7a cb a0 ab e4 5c 7b c1 |
| DigiCert Inc | Thawte EV RSA CA 2018 | 9e 84 8f 52 57 5c 6b 1a 69 d6 ab 62 e0 28 8b fa d4 a5 56 4e |
| DigiCert | Microsoft Azure TLS Issuing CA 02 | e7 ee a6 74 ca 71 8e 3b ef d9 08 58 e0 9f 83 72 ad 0a e2 aa |
| GlobalSign (AlphaSSL) | AlphaSSL CA - SHA256 - G4 | d3 41 62 62 72 7f e1 82 e0 99 6c 79 3b 0f a4 46 76 c6 54 1a |
| DigiCert | DigiCert SHA2 Secure Server CA | 62 6d 44 e7 04 d1 ce ab e3 bf 0d 53 39 74 64 ac 80 80 14 2c |
| DigiCert | Encryption Everywhere DV TLS CA - G2 | ed 63 02 68 4a 32 59 aa 04 f1 0f e9 a9 7a 8f d3 0b 96 5d 26 |
| RapidSSL TLS RSA CA G1 | RapidSSL TLS RSA CA G1 | cb fe 9e b4 3b 3b 37 fe 0d fb c4 c2 eb 2d 4e 07 d0 8b d8 e8 |
| Amazon | Amazon RSA 2048 M01 | 2a d9 74 a7 75 f7 3c bd bb d8 f5 ac 3a 49 25 5f a8 fb 1f 8c |
| COMODO CA | Network Solutions OV Server CA 2 | 44 0f f6 8a 35 e0 39 95 ac 55 e4 57 a6 7e b1 68 0f 9a 7c dd |
| DIGICERT | GeoTrust RSA CN CA G2 | 7d f1 c5 f3 c9 46 9a 05 bf 61 d5 64 c5 20 2f 20 ee e0 72 10 |
| DigiCert CN RSA EV CA G1 | DigiCert CN RSA EV CA G1 | 03 09 bf 53 d2 b7 5b c6 b3 ef 5f 33 7f 51 ee ba 1f 99 68 85 |
| DIGICERT | DigiCert Global G2 TLS RSA SHA256 2020 CA1 | 1b 51 1a be ad 59 c6 ce 20 70 77 c0 bf 0e 00 43 b1 38 26 12 |
| Sectigo | Network Solutions RSA DV SSL CA 3 | ec 86 c3 53 d7 ac b5 4d e7 6f 11 64 79 14 e8 f3 84 c5 e6 a3 |
| Sectigo | Corporation Service Company RSA OV SSL CA | d7 2c af 0e f1 a2 ea f2 f5 fe e5 cc fd 74 28 a3 20 41 84 18 |
| DigiCert | DigiCert TLS RSA SHA256 2020 CA1 | 1c 58 a3 a8 51 8e 87 59 bf 07 5b 76 b7 50 d4 f2 df 26 4f cd |
| Gandi RSA Domain Validation | Gandi | a5 e9 a8 a4 2b 69 1c 08 bd 9e e5 d6 86 dd 69 c3 71 44 98 dd |
| COMODO CA | InCommon RSA Server CA 2 | 78 e5 02 62 e8 c4 75 71 fb 82 d5 06 3a 6c 9b d9 1b b8 a3 25 |
| Let's Encrypt | R10 | 00 ab ef d0 55 f9 a9 c7 84 ff de ab d1 dc dd 8f ed 74 14 36 |
| Let's Encrypt | R11 | 69 6d b3 af 0d ff c1 7e 65 c6 a2 0d 92 5c 5a 7b d2 4d ec 7e |
| Sectigo | USERTrust RSA Certification Authority | a0 42 a8 52 96 1b 90 d5 86 75 91 d0 ea 2b 99 6c b9 ec fe f1 |
| Sectigo | USERTrust RSA Certification Authority | d7 fd 69 70 5c bb 61 70 80 66 ff 39 a5 62 d7 37 e4 ea 77 ce |
| Amazon | Amazon Root CA 1 | d9 fe 0a 65 fa 00 ca bf 61 f5 12 0d 37 3a 81 35 e1 46 1f 15 |
| Sectigo | COMODO RSA Domain Validation Secure Server CA | 33 9c dd 57 cf d5 b1 41 16 9b 61 5f f3 14 28 78 2d 1d a6 39 |
| DigiCert | GeoTrust EV RSA CA G2 | 68 7d 4a 4d 47 01 4f 91 21 7e 4a 06 2b bf 9d 23 83 58 94 3e |
| Amazon | Amazon RSA 2048 M02 | 41 4a 20 60 b7 38 c6 35 cc 7f c2 43 e0 52 61 55 92 83 0c 53 |
| Sectigo | Network Solutions RSA OV SSL CA 3 | 36 df 3f 8f 70 59 10 74 50 b9 63 cc 39 87 7d 4c a4 43 a0 db |
| DigiCert | GeoTrust G2 TLS CN RSA4096 SHA256 2022 CA1 | 57 f1 a4 7c 5b c0 67 7b 70 a0 92 57 2e d8 c9 28 5b db ee aa |
| DigiCert | DigiCert Assured G2 SMIME RSA4096 SHA384 2024 CA1 | 67 c9 fb 1e 60 3c fd d4 af b6 c6 9e a5 07 f7 4d 6c 6a 6a 76 |
| DigiCert | DigiCert Secure Site OV G2 TLS CN RSA4096 SHA256 2022 CA1 | 92 bc c5 2c 87 f8 30 eb 7a ab f7 db 77 8c de d1 ab 1c 28 d8 |
| Sectigo | Trusted Secure Certificate Authority DV | 9b 8b 0a f7 e1 2f 6c 4f c6 c2 f8 2d bf d5 5b ba 47 00 e8 fc |
| DigiCert | Microsoft Azure RSA TLS Issuing CA 03 | f9 38 8e a2 c9 b7 d6 32 b6 6a 2b 0b 40 6d f1 d3 7d 39 01 f6 |
| GlobalSign | GlobalSign GCC R3 OV TLS CA 2024 | 73 28 b0 27 c7 e2 13 9e e3 ba 57 b5 28 cd b3 57 f8 e3 b9 d0 |
| JPMC | JPMC Application Policy Authority-G1 | 1d 0e e4 3a e6 85 68 28 23 ab 43 70 17 ac 56 1b 64 61 c9 f1 |
| JPMC | JPMC NotProd Application Identity Authority-2-G1 | bb ba de 7e b5 de 94 bd a1 4a 49 f8 85 0a be ca 95 5c 91 36 |
| GlobalSign | GlobalSign GCC R3 EV QWAC CA 2020 | ed d4 c6 4d fd 0e 38 d5 86 f1 c2 f0 a9 2d f0 a4 11 35 1f 8f |
| Sectigo | GoGetSSL RSA DV CA | 07 0a 72 6c 6e 44 18 dc f0 21 38 74 f0 c1 6d 93 b0 41 e9 35 |
| DigiCert | Microsoft Azure RSA TLS Issuing CA 04 | be 68 d0 ad aa 23 45 b4 8e 50 73 20 b6 95 d3 86 08 0e 5b 25 |
| DigiCert | Microsoft Azure RSA TLS Issuing CA 08 | 31 60 09 91 ed 5f ec 63 d3 55 a5 48 4a 6d cc 78 7e ad 89 bc |
| JPMC | JPMC Application Identity Authority-3-G1 | cc 3c c9 00 2d f7 35 ec 80 62 4e 52 5d 04 45 c9 6d 16 a2 e9 |
| GlobalSign | GlobalSign GCC R6 AlphaSSL CA 2023 | 58 f6 a6 8d 38 86 7d 61 b3 46 f3 bb 29 8b cb 0f cd d3 0a 99 |
| Sectigo | Entrust OV TLS Issuing RSA CA 2 | 56 a4 ad 24 d7 16 c8 b2 35 eb bf 47 fd aa 40 04 42 9b d7 20 |
| GlobalSign | WE1 | 41 80 da e3 d4 f9 b3 b0 aa ee bf 2a 9a 71 33 26 89 83 28 84 |
| DigiCert | DigiCert Secure Site Pro EV G2 TLS CN RSA4096 SHA256 2022 CA1 | b9 17 ae a3 73 ab e3 cf 50 86 12 dd bf 90 d7 6a 80 30 c6 36 |
| DigiCert Global Root G2 | TrustAsia DV TLS RSA CA 2025 | 7b 8a 18 d5 5f a2 ea 49 34 b8 d0 2d 0a 27 c0 c6 34 c2 49 94 |
| JPMCROOTCA | JPMC Application Policy Authority-G1 | 29 1b ee 24 7c cb 96 18 49 03 c0 8f 4d 26 63 20 1d 13 60 78 |
| SSL.com | Entrust OV TLS Issuing RSA CA 1 | ca aa c3 e1 6b d2 42 66 88 7c c8 56 73 c0 18 f4 6a 13 9b 0f |
| SSL.com | SSL.com TLS RSA Root CA 2022 | 72 b2 76 44 bd 09 46 bf 3c 51 0c 00 0f 44 30 16 8f e2 89 8a |
| Google Trust Services LLC | WR1 | 41 f0 91 69 2f 3b 70 80 3b d1 fd 77 e9 29 63 d1 13 71 8c d2 |
| Sectigo | Sectigo Public Server Authentication CA EV R36 | 99 24 ca 17 90 c9 18 ab 1a 43 b7 ad 9b 4f a1 60 06 fb ae dc |
| Sectigo | Sectigo Public Server Authentication CA DV R36 | dd 55 b4 52 02 91 e2 76 58 8f 0d d0 2f af d8 3a 73 68 e0 fa |
| Sectigo | Sectigo Public Server Authentication CA OV R36 | 32 1c a0 56 e4 e4 8d 57 f1 79 a3 bd de cb c5 21 3b 99 16 c0 |
| DigiCert | DigiCert Basic OV G2 TLS CN RSA4096 SHA256 2022 CA1 | 60 70 72 70 f2 10 0e e2 b7 71 fe c9 ef fa d8 c9 bf fe 33 58 |
| JPMC | JPMC Application Identity Authority-1-G1 | ab 87 a2 35 33 1e 23 64 43 ad 4d d1 26 32 94 0f 7a 31 9d 2a |
| DigiCert | DigiCert G5 TLS RSA4096 SHA384 2021 CA1 | 81 5c d8 ff 64 be ac e0 7e f8 f2 f9 d5 33 01 1f a4 79 36 58 |
| Let's Encrypt | E6 | c9 4d c4 83 1a 90 1a 9f ec 0f b4 9b 71 bd 49 b5 aa d4 fa d0 |
| JPMC | JPMC Application Policy Authority-G1 | 25 0a 3f 78 b9 6a 60 7a d0 4b 77 93 a8 a4 74 af a6 f8 ee 8d |
| Sectigo | Sectigo RSA Document Signing CA | ba 1c 71 82 42 f1 b4 66 11 c8 42 5b ff 6f 7a a0 4f 38 1f ca |
| JPMC | JPMC Application Identity Authority-2-G1 | cd 99 bf 39 12 64 4d c7 2d d8 5f 48 ae 6a 05 2d 28 42 77 9c |
| Let's Encrypt | R13 | 22 ff 89 58 65 61 fc 2d 52 f7 74 91 e9 f1 ef f1 b8 0b e3 3e |
| Let's Encrypt | R12 | ee 44 78 28 35 d8 fb 31 39 4d a5 ce b8 40 dc 93 84 9b cf 5a |
| DigiCert Global G3 | DigiCert Global G3 TLS ECC SHA384 2020 CA1 | 95 77 f9 1f e8 6c 27 d9 91 21 29 73 0e 81 66 37 3f c2 ee b8 |
| DigiCert | DigiCert Document Signing CA | fb 3a 7f 7c 9d e7 30 60 09 4f b2 65 e3 76 f2 ca 86 da 23 40 |
| Starfield | Starfield Secure Certificate Authority - G2 | 7e dc 37 6d cf d4 5e 6d df 08 2c 16 0d f6 ac 21 83 5b 95 d4 |
Next steps
- Review J.P. Morgan API specifications.SHA-1 Thumbprint